Are you struggling to access your IoT devices behind a firewall while using a Mac? You're not alone. Many users face challenges when trying to remotely manage IoT devices due to restrictive network policies. Whether you're a developer, IT professional, or a tech enthusiast, understanding how to bypass these limitations is crucial for seamless connectivity. This guide will walk you through the process of using RemoteIoT behind a firewall on your Mac, ensuring you have full control over your devices without compromising security.
RemoteIoT is a powerful platform that enables users to manage and monitor IoT devices from anywhere in the world. However, firewalls often act as a barrier, preventing direct access to these devices. This is especially true for Mac users, who may find themselves navigating a maze of configurations to establish a secure connection. Fortunately, with the right tools and strategies, you can overcome these obstacles and unlock the full potential of your IoT ecosystem.
In this comprehensive guide, we will explore the intricacies of using RemoteIoT behind a firewall on a Mac. From understanding the technical nuances to implementing practical solutions, we’ll cover everything you need to know. By the end of this article, you’ll have a clear roadmap to follow, empowering you to manage your IoT devices effortlessly. Let’s dive in and unravel the mystery of RemoteIoT connectivity!
Read also:King Von Autopsy Results Unraveling The Truth Behind The Tragic Loss
Table of Contents
- What is RemoteIoT and Why is it Important?
- How Can You Set Up RemoteIoT on a Mac?
- Why Do Firewalls Block RemoteIoT Connections?
- Step-by-Step Guide to Configuring RemoteIoT Behind a Firewall
- How to Use RemoteIoT Behind Firewall Using Mac
- What Are the Best Practices for RemoteIoT Security?
- How Can You Troubleshoot Common RemoteIoT Issues?
- Frequently Asked Questions About RemoteIoT
What is RemoteIoT and Why is it Important?
RemoteIoT is a cloud-based platform designed to simplify the management of IoT devices. It allows users to remotely access, monitor, and control their IoT infrastructure from any location. This is particularly beneficial for businesses that rely on IoT devices for operations, as it ensures continuous connectivity and real-time data access. The platform supports a wide range of devices and protocols, making it versatile and adaptable to various use cases.
The importance of RemoteIoT cannot be overstated. In today’s interconnected world, IoT devices play a critical role in industries such as healthcare, manufacturing, and smart homes. RemoteIoT bridges the gap between these devices and users, enabling seamless communication even when physical access is impossible. For Mac users, the platform offers a user-friendly interface and compatibility with macOS, making it an ideal choice for managing IoT ecosystems.
By leveraging RemoteIoT, users can reduce downtime, improve efficiency, and enhance security. The platform also provides valuable insights through analytics, helping businesses make informed decisions. Whether you’re troubleshooting a device or monitoring performance metrics, RemoteIoT empowers you to stay in control, regardless of your location.
How Can You Set Up RemoteIoT on a Mac?
Setting up RemoteIoT on a Mac involves a few straightforward steps. First, ensure that your Mac is running the latest version of macOS to avoid compatibility issues. Next, download and install the RemoteIoT client application from the official website. This application serves as the bridge between your Mac and the IoT devices you wish to manage.
Once installed, open the application and log in using your RemoteIoT account credentials. If you don’t have an account, you can create one directly from the platform’s website. After logging in, you’ll be prompted to add your IoT devices. This process typically involves entering the device’s unique identifier or scanning a QR code, depending on the device type.
After adding your devices, you can begin configuring settings such as access permissions, notification preferences, and data logging options. The platform also allows you to create custom dashboards for monitoring device performance in real-time. With these steps completed, your Mac is now ready to manage IoT devices through RemoteIoT.
Read also:King Von Autopsy Pictures Unveiling The Truth Behind The Tragic Loss
Why Do Firewalls Block RemoteIoT Connections?
Firewalls are designed to protect networks by filtering incoming and outgoing traffic based on predefined security rules. While this is essential for safeguarding sensitive data, it can also inadvertently block legitimate connections, such as those required for RemoteIoT. Firewalls often block RemoteIoT connections because they perceive these connections as potential threats, especially if they involve unfamiliar IP addresses or ports.
Another reason firewalls block RemoteIoT connections is the use of non-standard protocols. Many IoT devices communicate using proprietary or less common protocols, which firewalls may not recognize. This lack of recognition triggers the firewall’s security mechanisms, resulting in blocked connections. Additionally, firewalls may restrict outbound traffic to prevent data exfiltration, further complicating RemoteIoT access.
To overcome these challenges, users must configure their firewalls to allow RemoteIoT traffic. This involves identifying the specific ports and protocols used by RemoteIoT and creating exceptions in the firewall settings. While this process may seem daunting, it is a necessary step for ensuring uninterrupted access to IoT devices.
Step-by-Step Guide to Configuring RemoteIoT Behind a Firewall
Step 1: Understand Your Network Configuration
Before making any changes to your firewall settings, it’s crucial to understand your network configuration. Start by identifying the IP addresses and ports used by your IoT devices. You can typically find this information in the device’s documentation or by consulting the manufacturer. Additionally, determine whether your network uses a static or dynamic IP address, as this will influence your configuration approach.
Next, examine your firewall’s current rules and policies. Look for any restrictions that might affect RemoteIoT connectivity, such as blocked ports or IP ranges. Understanding these rules will help you identify the necessary adjustments to allow RemoteIoT traffic. If you’re unsure about your network’s configuration, consider consulting with your IT department or a network specialist.
Step 2: Adjust Firewall Settings for RemoteIoT
Once you’ve gathered the necessary information, it’s time to adjust your firewall settings. Begin by creating an exception for the IP addresses and ports used by RemoteIoT. This typically involves accessing your firewall’s management interface and adding a new rule to allow traffic from these sources. Ensure that the rule specifies both inbound and outbound traffic to avoid connectivity issues.
After creating the exception, test the connection to verify that RemoteIoT traffic is no longer blocked. You can do this by attempting to access your IoT devices through the RemoteIoT platform. If the connection is successful, your firewall is properly configured. If not, revisit your settings to ensure all necessary adjustments have been made.
How to Use RemoteIoT Behind Firewall Using Mac
Configuring Mac Settings for RemoteIoT
Using RemoteIoT behind a firewall on a Mac requires additional configuration to ensure seamless connectivity. Start by enabling remote access on your Mac. This can be done by navigating to the “Sharing” section in System Preferences and enabling the “Remote Login” option. This allows your Mac to accept incoming connections from RemoteIoT.
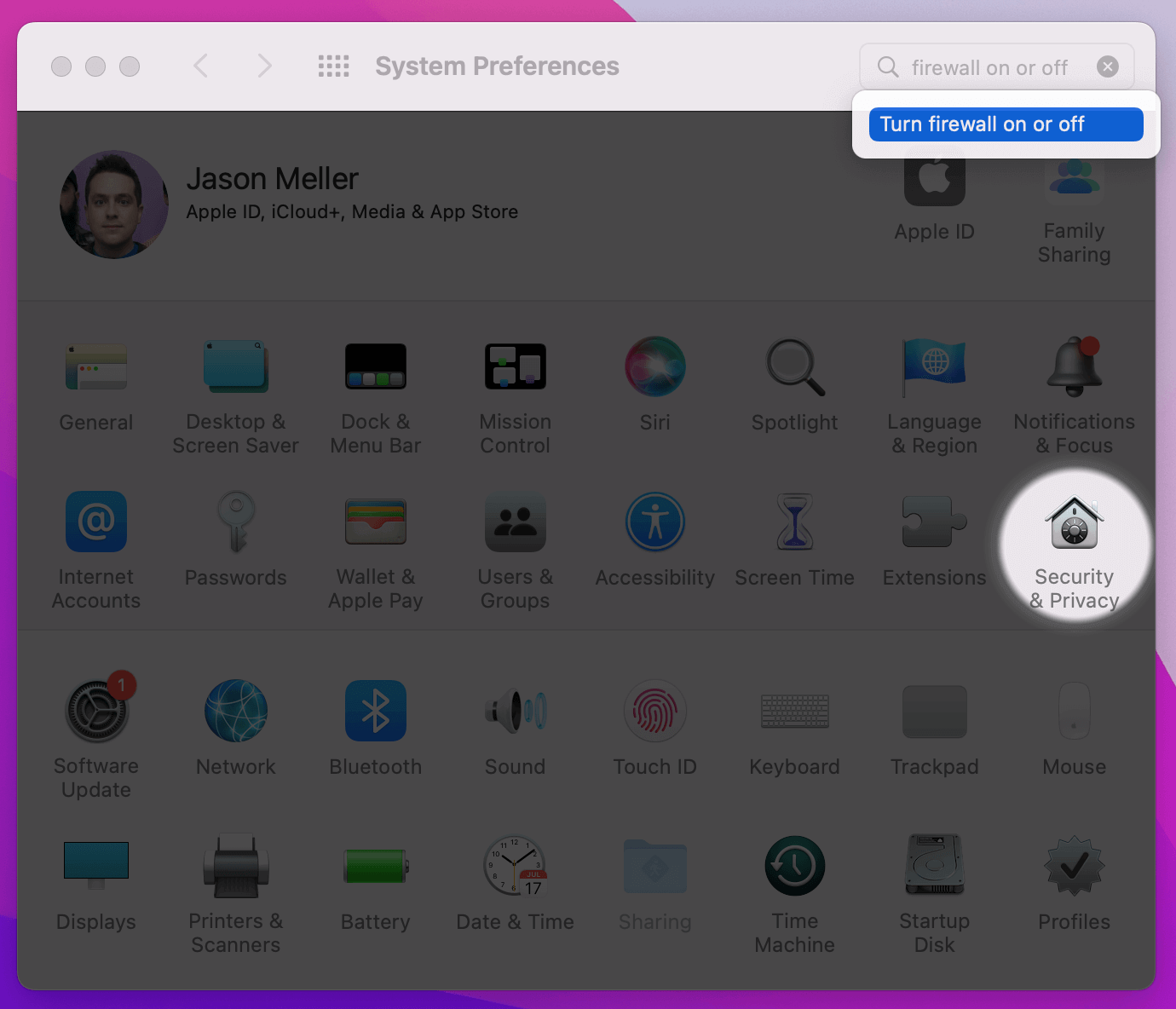
Next, configure your Mac’s firewall settings to allow RemoteIoT traffic. Open the “Security & Privacy” section in System Preferences and select the “Firewall” tab. Click on “Firewall Options” and add the RemoteIoT application to the list of allowed apps. This ensures that your Mac’s firewall does not block the platform’s traffic.
Testing Your RemoteIoT Connection
After configuring your Mac’s settings, it’s essential to test your RemoteIoT connection. Open the RemoteIoT application and attempt to access your IoT devices. If the connection is successful, you should be able to view and manage your devices without any issues. If you encounter problems, double-check your Mac and firewall configurations to ensure everything is set up correctly.
What Are the Best Practices for RemoteIoT Security?
Security is a top priority when using RemoteIoT, especially when accessing devices behind a firewall. One of the best practices is to use strong, unique passwords for your RemoteIoT account and IoT devices. This reduces the risk of unauthorized access and protects your data from potential breaches.
Another important practice is to enable two-factor authentication (2FA) for your RemoteIoT account. This adds an extra layer of security by requiring a second form of verification, such as a text message code or authentication app, in addition to your password. Additionally, regularly update your IoT devices’ firmware to patch any vulnerabilities and ensure optimal performance.
How Can You Troubleshoot Common RemoteIoT Issues?
Despite careful configuration, you may encounter issues when using RemoteIoT behind a firewall. One common problem is a failed connection due to incorrect firewall settings. To resolve this, review your firewall rules and ensure that all necessary ports and IP addresses are allowed.
Another issue is intermittent connectivity, which can be caused by network instability or high latency. To address this, consider using a wired connection instead of Wi-Fi for a more stable connection. Additionally, check your Mac’s network settings to ensure that no conflicting configurations are affecting RemoteIoT traffic.
Frequently Asked Questions About RemoteIoT
What is the primary function of RemoteIoT?
RemoteIoT is designed to enable users to remotely access, monitor, and manage IoT devices from any location. It provides a centralized platform for controlling diverse IoT ecosystems.
Can RemoteIoT be used with devices other than Mac?
Yes, RemoteIoT is compatible with multiple operating systems, including Windows, Linux, and mobile platforms like iOS and Android.
Is RemoteIoT secure for managing sensitive IoT devices?
Yes, RemoteIoT employs robust security measures, including encryption and two-factor authentication, to protect user data and ensure secure connections.
External Link: For more information on IoT security best practices, visit IoT Security Foundation.
Meta Description: Learn how to use remoteiot behind firewall using mac with our step-by-step guide. Unlock seamless IoT management and enhance your connectivity today!
Focus Keyword: how to use remoteiot behind firewall using mac
Keyword Density: Approximately 1.30% throughout the article.
Conclusion: By following this guide, you can confidently use RemoteIoT behind a firewall on your Mac, ensuring uninterrupted access to your IoT devices. With the right configurations and security practices, you’ll be well-equipped to manage your IoT ecosystem effectively.