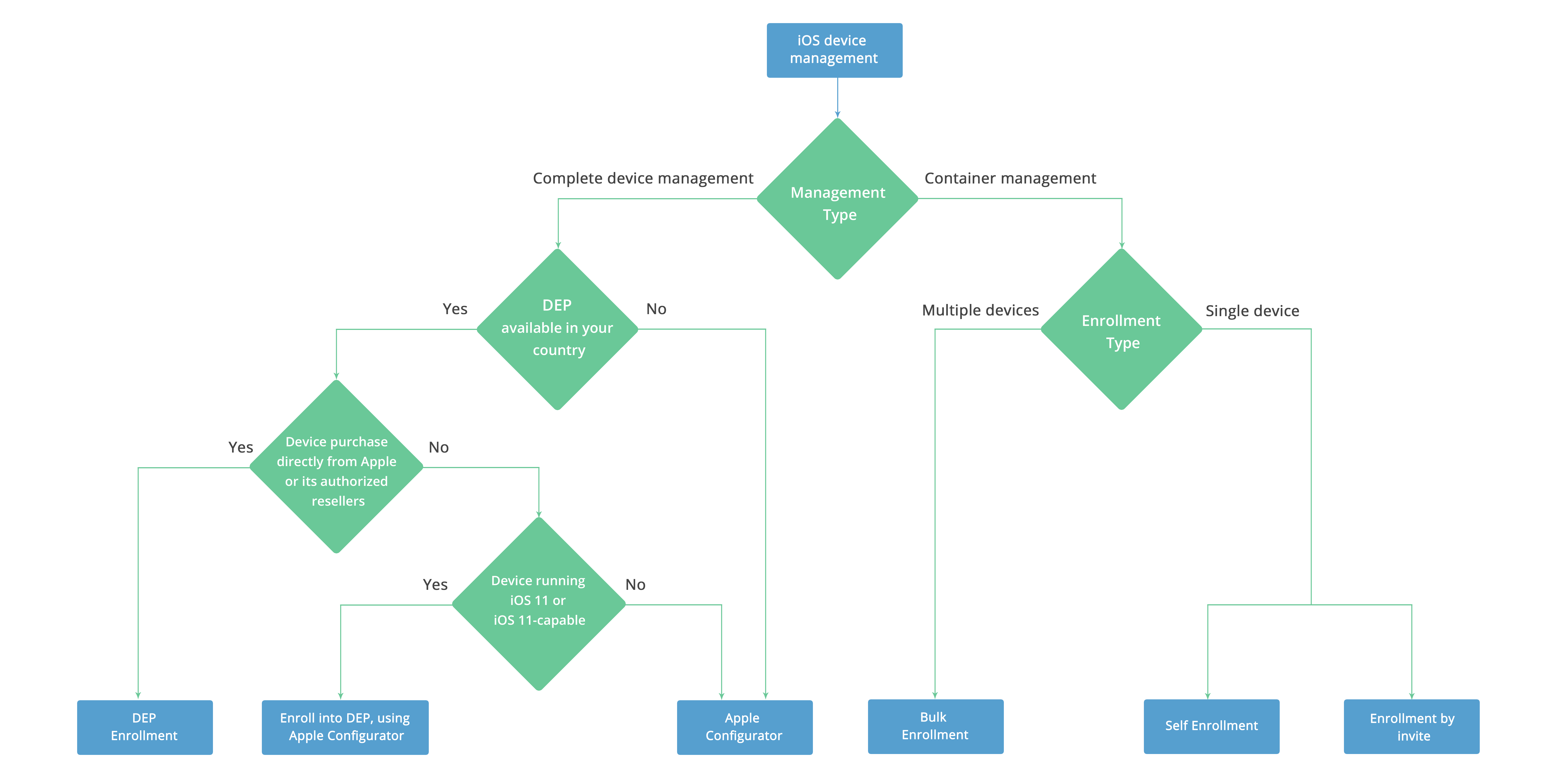
From smart homes to industrial automation, the proliferation of IoT devices has created unprecedented opportunities and challenges for businesses and individuals alike. RemoteIoT device management has emerged as a critical solution, enabling seamless control and monitoring of distributed devices from anywhere in the world. This remoteiot device management tutorial will guide you through the fundamental concepts, practical applications, and advanced strategies to harness the full potential of IoT ecosystems. As we delve deeper into the realm of remote IoT management, it becomes evident that proper device oversight is crucial for maintaining security, optimizing performance, and ensuring operational efficiency. The complexity of managing hundreds or thousands of devices across different locations requires specialized tools and methodologies. Through this comprehensive remoteiot device management tutorial, you'll discover how to implement robust management protocols, automate routine tasks, and troubleshoot common issues that arise in IoT networks. We'll explore both theoretical foundations and practical implementation strategies that cater to various industry needs. The importance of mastering RemoteIoT device management cannot be overstated in our increasingly digital landscape. Whether you're an IT professional seeking to enhance your organization's IoT infrastructure or a technology enthusiast looking to optimize your smart home setup, this remoteiot device management tutorial will provide valuable insights and actionable steps. By the end of this comprehensive guide, you'll possess the knowledge and tools necessary to implement effective device management strategies that align with your specific requirements and objectives.
Table of Contents
- What Are the Core Components of RemoteIoT Device Management?
- How Does RemoteIoT Device Management Enhance Security?
- What Are the Benefits of Implementing RemoteIoT Device Management?
Understanding Device Provisioning and Configuration
Optimizing Remote Monitoring and Maintenance
- Exploring Advanced Features in RemoteIoT Platforms
- Implementing Effective Firmware Update Strategies
- Creating a Robust RemoteIoT Management Workflow
How to Troubleshoot Common RemoteIoT Issues?
What Are the Best Practices for RemoteIoT Device Management?
What Are the Core Components of RemoteIoT Device Management?
Understanding the fundamental building blocks of remoteiot device management tutorial is crucial for establishing a successful IoT infrastructure. At its core, RemoteIoT device management comprises several interconnected components that work in harmony to ensure seamless operation and control. The first essential element is device provisioning, which involves the initial setup and registration of IoT devices within the management ecosystem. This process typically includes secure authentication mechanisms, device identification protocols, and initial configuration settings that establish the foundation for future management activities. Monitoring and diagnostics represent another critical component in the remoteiot device management tutorial framework. Modern IoT management platforms provide real-time visibility into device performance metrics, network status, and operational parameters. These monitoring capabilities enable administrators to track device health, detect anomalies, and prevent potential issues before they escalate. The data collected through continuous monitoring also serves as valuable input for optimizing device performance and improving overall system efficiency. Software and firmware management forms the third pillar of effective remoteiot device management tutorial. This component encompasses the ability to remotely update device software, apply security patches, and implement feature enhancements across the entire IoT network. The importance of this capability cannot be overstated, as it ensures devices remain up-to-date with the latest security protocols and functionality improvements. Additionally, configuration management tools allow administrators to maintain consistent settings across devices, enforce compliance policies, and implement changes across multiple devices simultaneously. The final core component involves security management and access control. Robust remoteiot device management tutorial systems incorporate multiple layers of security measures, including encryption protocols, access control lists, and threat detection mechanisms. These security features work together to protect devices from unauthorized access, prevent data breaches, and ensure the integrity of IoT operations. The integration of these core components creates a comprehensive management ecosystem that enables efficient oversight and control of distributed IoT devices.
How Does RemoteIoT Device Management Enhance Security?
Security remains one of the most critical aspects of remoteiot device management tutorial, especially in today's landscape of increasing cyber threats. Effective security management begins with robust authentication protocols that verify device identity before granting access to the management network. Modern RemoteIoT platforms employ multi-factor authentication methods, digital certificates, and secure boot processes to ensure only authorized devices can connect to the system. These measures create the first line of defense against unauthorized access attempts and potential security breaches. Data encryption plays a vital role in maintaining secure communications between IoT devices and management platforms. Through advanced encryption standards and secure communication protocols, remoteiot device management tutorial systems protect sensitive information during transmission. This includes encrypting device telemetry data, management commands, and firmware updates to prevent interception or tampering by malicious actors. Additionally, secure storage mechanisms ensure that sensitive configuration data and credentials remain protected even when stored on devices. The implementation of comprehensive security monitoring and threat detection capabilities further enhances the protection offered by remoteiot device management tutorial. These systems employ sophisticated algorithms and machine learning techniques to analyze device behavior patterns and detect anomalies that may indicate security threats. Real-time alerting mechanisms notify administrators of potential security incidents, enabling rapid response and mitigation. Regular security audits and vulnerability assessments help maintain a proactive security posture, while automated patch management ensures devices receive timely security updates to address newly discovered vulnerabilities.
Read also:Harris Faulkner A Trailblazer In Journalism And Media
What Are the Benefits of Implementing RemoteIoT Device Management?
Implementing a comprehensive remoteiot device management tutorial approach yields numerous advantages that extend beyond basic device control. One of the most significant benefits is the substantial reduction in operational costs achieved through automated management processes. By centralizing device oversight and automating routine maintenance tasks, organizations can significantly decrease manual intervention requirements and associated labor expenses. The ability to perform remote troubleshooting and configuration changes eliminates the need for on-site visits, resulting in considerable savings in both time and resources. Scalability represents another crucial advantage of adopting remoteiot device management tutorial strategies. As IoT deployments grow in size and complexity, effective management systems enable seamless scaling without compromising performance or security. Modern management platforms can handle thousands of devices simultaneously, maintaining consistent oversight and control across expanding networks. This scalability ensures that businesses can adapt to changing requirements and expand their IoT infrastructure without encountering management bottlenecks or performance degradation. The implementation of remoteiot device management tutorial also leads to improved operational efficiency through enhanced visibility and control. Real-time monitoring capabilities provide administrators with comprehensive insights into device performance, network status, and system health. This visibility enables proactive maintenance, optimized resource allocation, and data-driven decision-making. Furthermore, the ability to implement standardized configurations and automated workflows ensures consistent device behavior across the entire IoT ecosystem, reducing configuration errors and improving overall system reliability.
Understanding Device Provisioning and Configuration
Device provisioning and configuration form the foundation of successful remoteiot device management tutorial implementation. The provisioning process begins with device enrollment, where new devices are securely registered within the management ecosystem. This involves generating unique device identifiers, establishing secure communication channels, and applying initial configuration settings. Modern provisioning methods often utilize zero-touch deployment techniques, allowing devices to automatically connect to the management platform upon activation without requiring manual intervention. Configuration management plays a crucial role in maintaining consistent device behavior across the IoT network. Through centralized configuration tools, administrators can define and enforce standardized settings for all managed devices. These configuration profiles typically include network parameters, security settings, operational parameters, and application-specific configurations. The ability to apply configuration changes across multiple devices simultaneously streamlines management processes and ensures uniformity across the IoT ecosystem. Additionally, configuration versioning features enable administrators to track changes, revert to previous settings if necessary, and maintain detailed audit trails of all configuration modifications.
Optimizing Remote Monitoring and Maintenance
Remote monitoring and maintenance capabilities represent a cornerstone of effective remoteiot device management tutorial strategies. Advanced monitoring systems provide comprehensive visibility into various device metrics, including CPU utilization, memory usage, network connectivity, and battery status. This data is typically presented through intuitive dashboards that display real-time information and historical trends, enabling administrators to quickly identify potential issues and optimize device performance. The implementation of threshold-based alerting systems ensures timely notifications when devices exceed predefined performance parameters or encounter operational anomalies. Predictive maintenance capabilities have revolutionized traditional maintenance approaches in remoteiot device management tutorial. By analyzing historical performance data and applying machine learning algorithms, these systems can predict potential failures before they occur. This predictive approach enables proactive maintenance scheduling, reducing unexpected downtime and extending device lifespan. Additionally, remote troubleshooting features allow administrators to diagnose and resolve issues without physical access to devices, significantly reducing resolution times and maintenance costs. The integration of automated maintenance routines further enhances efficiency by performing routine checks and applying necessary updates during optimal maintenance windows.
Exploring Advanced Features in RemoteIoT Platforms
Modern RemoteIoT platforms offer a sophisticated array of advanced features that significantly enhance the capabilities of remoteiot device management tutorial. One of the most impactful advancements is the integration of artificial intelligence and machine learning algorithms. These technologies enable predictive analytics, anomaly detection, and automated decision-making processes that optimize device performance and resource allocation. For instance, AI-driven systems can analyze usage patterns to automatically adjust device settings, conserve energy, and improve operational efficiency across the IoT network. Another crucial advancement in remoteiot device management tutorial is the implementation of edge computing capabilities. By processing data locally on devices or nearby edge servers, these platforms reduce latency, minimize bandwidth consumption, and enhance real-time responsiveness. This edge computing architecture enables faster decision-making and more efficient data handling, particularly for time-sensitive applications. Additionally, the integration of containerization technologies allows for flexible deployment of applications and services directly on IoT devices, facilitating easier updates and maintenance. The incorporation of digital twin technology represents another significant advancement in remoteiot device management tutorial. Digital twins create virtual replicas of physical devices, enabling comprehensive simulation, testing, and analysis without affecting actual device operations. These virtual models allow administrators to test configuration changes, simulate failure scenarios, and optimize performance parameters in a risk-free environment. Furthermore, advanced visualization tools provide comprehensive insights into device relationships and network topology, helping administrators understand complex IoT ecosystems and optimize their architecture.
Implementing Effective Firmware Update Strategies
Developing and executing robust firmware update strategies is a critical component of successful remoteiot device management tutorial. The firmware update process must balance the need for timely security patches with the requirement for minimal operational disruption. Modern RemoteIoT platforms employ sophisticated update mechanisms that include delta updates, which transmit only the changed portions of firmware rather than complete packages. This approach significantly reduces bandwidth requirements and speeds up the update process, particularly important for large-scale IoT deployments. A successful remoteiot device management tutorial approach to firmware updates incorporates several key elements. First, update scheduling capabilities allow administrators to define optimal update windows based on device usage patterns and operational requirements. These scheduling tools often include features for staggered rollouts, enabling gradual deployment across device groups to minimize the impact of potential issues. Additionally, rollback mechanisms provide essential safety nets, allowing devices to revert to previous firmware versions if updates cause unexpected problems. Security considerations play a crucial role in firmware update strategies within remoteiot device management tutorial. Secure update protocols ensure that only authorized updates are applied to devices, preventing unauthorized modifications or malicious code injection. Digital signatures verify update authenticity, while secure communication channels protect update packages during transmission. Furthermore, update validation processes confirm successful installation and proper device functionality before marking updates as complete, ensuring device integrity and operational continuity.
Creating a Robust RemoteIoT Management Workflow
Establishing an effective remoteiot device management tutorial workflow requires careful planning and systematic implementation of best practices. The workflow begins with comprehensive device inventory management, where each device is categorized, tagged, and assigned to specific groups based on its role and location. This organizational structure enables targeted management actions and facilitates efficient resource allocation across the IoT network. Implementing role-based access control ensures that different team members have appropriate levels of access and permissions, maintaining security while enabling efficient collaboration. The core of a robust remoteiot device management tutorial workflow involves establishing standardized operational procedures. These procedures include regular health checks, scheduled maintenance windows, and predefined response protocols for common issues. Automation plays a crucial role in streamlining these processes, with automated scripts handling routine tasks such as log collection, performance monitoring, and basic troubleshooting. The implementation of incident management systems helps track issues from detection to resolution, ensuring proper documentation and continuous improvement of management practices. Continuous improvement forms the final component of an effective remoteiot device management tutorial workflow. Regular review sessions help identify areas for optimization and adaptation to changing requirements. Performance metrics and key performance indicators (KPIs) provide valuable insights into management effectiveness, enabling data-driven decisions about workflow adjustments. Additionally, incorporating feedback loops from both technical teams and end-users ensures that the management workflow remains aligned with operational needs and technological advancements.
Read also:Remoteiot Vpc Price A Comprehensive Guide To Virtual Private Clouds
How to Troubleshoot Common RemoteIoT Issues?
Troubleshooting in remoteiot device management tutorial requires a systematic approach to identify and resolve issues efficiently. The first step involves leveraging comprehensive diagnostic tools provided by management platforms to gather detailed information about device status, network connectivity, and system logs. These tools often include automated health checks that can quickly identify common problems such as network interruptions, configuration errors, or resource exhaustion. When addressing connectivity issues, administrators should verify network settings, check firewall configurations, and examine routing tables to ensure proper communication paths. For performance-related problems in remoteiot device management tutorial, a methodical analysis of resource utilization metrics can reveal bottlenecks or misconfigurations. This includes examining CPU and memory usage patterns, disk space availability, and application performance indicators. Many issues can be resolved through configuration adjustments or resource reallocation, eliminating the need for device reboot or replacement. When dealing with firmware-related problems, the rollback feature becomes invaluable, allowing administrators to revert to previous stable versions while investigating the root cause of the issue.
What Are the Best Practices for RemoteIoT Device Management?
Implementing best practices