Businesses and individuals alike rely on platforms like RemoteIoT to ensure seamless connectivity while maintaining robust security protocols. One of the standout features of RemoteIoT is its ability to provide SSH key-based authentication, even for users who may not have prior experience with SSH keys. This ensures that users can securely access their devices without the hassle of managing complex passwords or worrying about unauthorized access. Whether you're managing IoT devices, servers, or other remote systems, understanding how to leverage the RemoteIoT platform SSH key free feature can significantly enhance your operational efficiency and security posture. The RemoteIoT platform offers a user-friendly interface that simplifies the process of generating and managing SSH keys, even for beginners. By eliminating the need for manual key generation or third-party tools, RemoteIoT empowers users to establish secure connections effortlessly. This is particularly beneficial for those who are new to remote device management or lack technical expertise. The platform’s SSH key free feature is designed to streamline the setup process, allowing users to focus on their core tasks without being bogged down by complicated security configurations. With RemoteIoT, you can rest assured that your devices are protected against unauthorized access, thanks to its state-of-the-art encryption protocols and intuitive design. Moreover, the RemoteIoT platform SSH key free functionality is not just about convenience—it’s about trust. By integrating cutting-edge security measures, RemoteIoT ensures that your data remains confidential and your devices stay secure. Whether you're managing a single IoT device or an entire fleet, the platform’s robust architecture and commitment to user-friendly security make it a top choice for businesses and individuals alike. In the sections that follow, we’ll delve deeper into how the platform works, explore its benefits, and provide practical tips for maximizing its potential.
Table of Contents
- What is RemoteIoT Platform SSH Key Free?
- How Does RemoteIoT SSH Key Free Work?
- Why Should You Use SSH Keys for Secure Access?
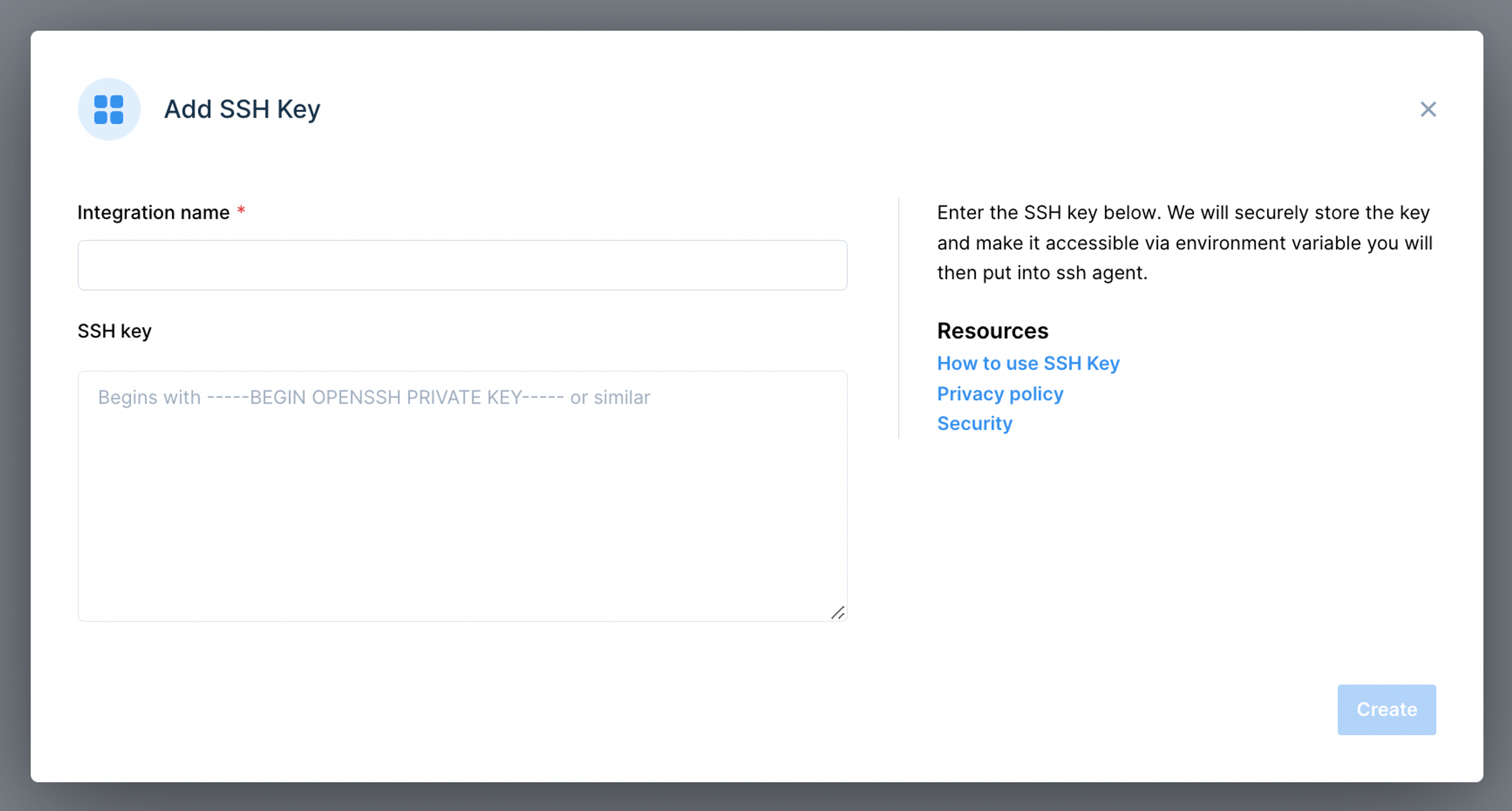
- How Can You Set Up RemoteIoT SSH Key Free?
- What Are the Benefits of Using RemoteIoT?
- Common Misconceptions About SSH Keys
- How to Troubleshoot SSH Key Issues?
- Frequently Asked Questions About RemoteIoT SSH Key Free
What is RemoteIoT Platform SSH Key Free?
The RemoteIoT platform SSH key free feature is a groundbreaking solution designed to simplify secure remote access for users of all technical backgrounds. SSH, or Secure Shell, is a cryptographic network protocol used to secure data communication and control devices over an unsecured network. Traditionally, setting up SSH keys requires technical expertise, as users must generate public and private key pairs, configure servers, and manage permissions. However, RemoteIoT eliminates these complexities by offering a streamlined, user-friendly interface that automates the process. This allows even beginners to establish secure connections without needing to manually generate or manage SSH keys. At its core, the RemoteIoT platform SSH key free feature operates by handling the key generation and configuration process on behalf of the user. When you sign up for the platform, it automatically generates a unique SSH key pair for your account. The public key is then deployed to your devices, while the private key remains securely stored within the platform. This ensures that only authorized users can access your devices, as the private key is never exposed or shared. The platform’s intuitive design ensures that users can activate this feature with just a few clicks, making it an ideal solution for businesses and individuals who prioritize both security and convenience. One of the standout aspects of the RemoteIoT platform SSH key free functionality is its versatility. Whether you're managing IoT devices, remote servers, or embedded systems, the platform adapts to your needs seamlessly. It supports a wide range of devices and operating systems, ensuring compatibility across diverse environments. Additionally, RemoteIoT’s SSH key free feature integrates advanced encryption protocols, such as RSA and ECDSA, to safeguard your data during transmission. This not only enhances security but also provides peace of mind, knowing that your devices are protected against unauthorized access and cyber threats.
How Does RemoteIoT SSH Key Free Work?
Understanding how the RemoteIoT platform SSH key free feature operates is essential for maximizing its potential. At a high level, the process involves three key components: key generation, device configuration, and secure access. Let’s break down each step to provide a clear picture of how the platform ensures seamless and secure connectivity.
Read also:Is Michael J Fox Still Alive Discover His Inspiring Journey And Legacy
Step 1: Creating an Account
When you sign up for the RemoteIoT platform, the system automatically generates a unique SSH key pair for your account. This eliminates the need for manual key generation, which can be a daunting task for users unfamiliar with SSH protocols. The platform uses industry-standard algorithms, such as RSA or ECDSA, to create these keys. The public key is stored on the RemoteIoT servers, while the private key remains securely encrypted within the platform. This separation ensures that only authorized users can access your devices, as the private key is never exposed or shared with third parties.
Step 2: Configuring Your Device
Once your account is set up, the next step is to configure your devices for secure access. RemoteIoT simplifies this process by providing step-by-step guidance through its user-friendly interface. You can add your devices to the platform by entering their IP addresses or hostnames. The platform then automatically deploys the public key to your devices, ensuring that they are ready for secure SSH connections. This eliminates the need for manual configuration, which can be time-consuming and error-prone. Additionally, RemoteIoT supports a wide range of devices and operating systems, making it easy to integrate into your existing infrastructure.
Ensuring Compatibility Across Devices
One of the standout features of RemoteIoT is its ability to adapt to diverse environments. Whether you're managing IoT devices, remote servers, or embedded systems, the platform ensures compatibility across various devices and operating systems. This versatility is achieved through its robust architecture, which supports protocols like SSH, HTTPS, and MQTT. By leveraging these protocols, RemoteIoT ensures that your devices remain accessible and secure, regardless of their location or configuration.
Advanced Encryption Protocols
Security is at the heart of the RemoteIoT platform SSH key free feature. The platform integrates advanced encryption protocols, such as RSA and ECDSA, to safeguard your data during transmission. These protocols ensure that your communications are encrypted end-to-end, protecting them from interception or tampering. Additionally, RemoteIoT employs state-of-the-art authentication mechanisms to verify the identity of users and devices. This multi-layered approach to security ensures that your devices remain protected against unauthorized access and cyber threats.
Why Should You Use SSH Keys for Secure Access?
SSH keys offer a level of security that traditional password-based authentication simply cannot match. Unlike passwords, which can be easily guessed, stolen, or brute-forced, SSH keys rely on complex cryptographic algorithms to authenticate users. This makes them virtually impossible to crack, even with advanced hacking tools. Additionally, SSH keys eliminate the need to remember or manage multiple passwords, reducing the risk of human error. By using the RemoteIoT platform SSH key free feature, you can leverage these benefits without the hassle of manual key generation or configuration.
What Are the Benefits of Using RemoteIoT?
The RemoteIoT platform offers a host of benefits that make it an ideal choice for secure remote access. First and foremost, its SSH key free feature simplifies the process of establishing secure connections, making it accessible to users of all technical backgrounds. Additionally, the platform’s user-friendly interface ensures that even beginners can manage their devices with ease. This is particularly beneficial for businesses that need to onboard new employees quickly or individuals who lack technical expertise. Another key advantage of RemoteIoT is its versatility. The platform supports a wide range of devices and operating systems, ensuring compatibility across diverse environments. This makes it easy to integrate into your existing infrastructure, regardless of your setup. Furthermore, RemoteIoT’s advanced encryption protocols and authentication mechanisms provide an additional layer of security, protecting your devices against unauthorized access and cyber threats.
Read also:Milton Augustine Williams Jr A Comprehensive Guide To His Life And Achievements
Common Misconceptions About SSH Keys
Despite their widespread use, SSH keys are often misunderstood. One common misconception is that they are difficult to set up and manage. While this may have been true in the past, platforms like RemoteIoT have simplified the process significantly. Another misconception is that SSH keys are only suitable for advanced users. In reality, the RemoteIoT platform SSH key free feature makes it easy for beginners to leverage the benefits of SSH keys without needing technical expertise.
How to Troubleshoot SSH Key Issues?
Even with the best tools, issues can arise when using SSH keys. Common problems include connection errors, authentication failures, and misconfigured devices. Fortunately, the RemoteIoT platform provides comprehensive troubleshooting guides and support to help users resolve these issues quickly. Additionally, the platform’s intuitive interface makes it easy to identify and fix configuration errors, ensuring that your devices remain accessible and secure.
Frequently Asked Questions About RemoteIoT SSH Key Free
Is the RemoteIoT Platform SSH Key Free Feature Really Free to Use?
Yes, the RemoteIoT platform SSH key free feature is completely free to use. The platform offers a range of free and paid plans, ensuring that users of all budgets can access its powerful features.
Can I Use RemoteIoT SSH Key Free with Multiple Devices?
Absolutely! The RemoteIoT platform supports multiple devices, making it easy to manage your entire fleet from a single interface.
How Secure Is the RemoteIoT SSH Key Free Feature?
The RemoteIoT platform SSH key free feature is highly secure, leveraging advanced encryption protocols and authentication mechanisms to protect your devices against unauthorized access.
In conclusion, the RemoteIoT platform SSH key free feature is a game-changer for secure remote access. By simplifying the process of setting up and managing SSH keys, it empowers users to focus on their core tasks without compromising on security. Whether you're a business owner, IT professional, or individual user, RemoteIoT offers a versatile and user-friendly solution that meets your needs. To learn more about how RemoteIoT can benefit you, visit their official website.